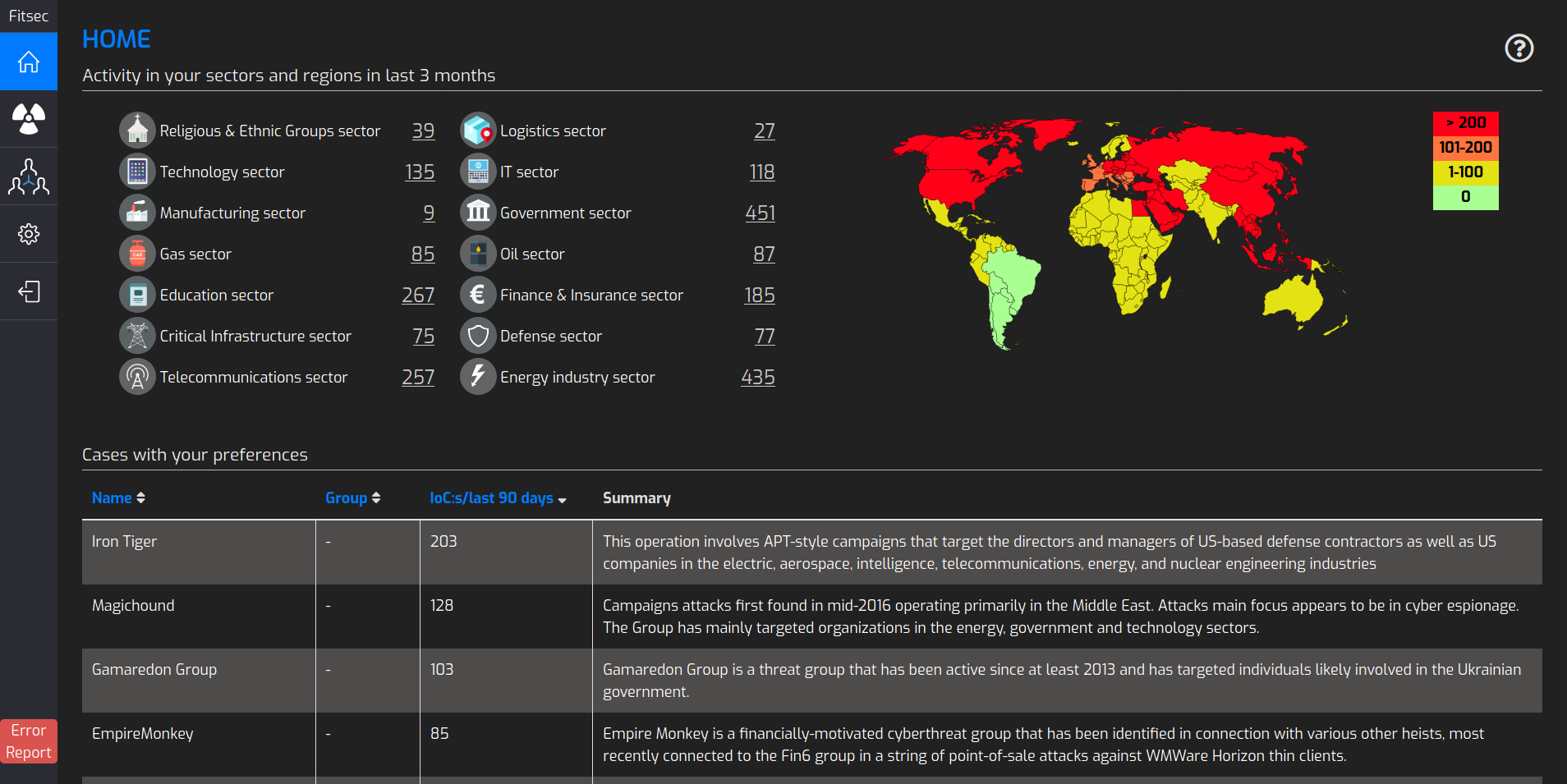
DDOS-Feed
The Fitsec DDOS feed offers intelligence on the latest DDOS threats and it reports on threats that are targeted against an organization's network infrastructure. The data provided by the DDOS feed includes malicious C2 (command and control) commands issued and the origin of the attack in real time.
The DDOS feed is especially beneficial to operators or other organizations that have critical online services and want to monitor the information security status of their networks.
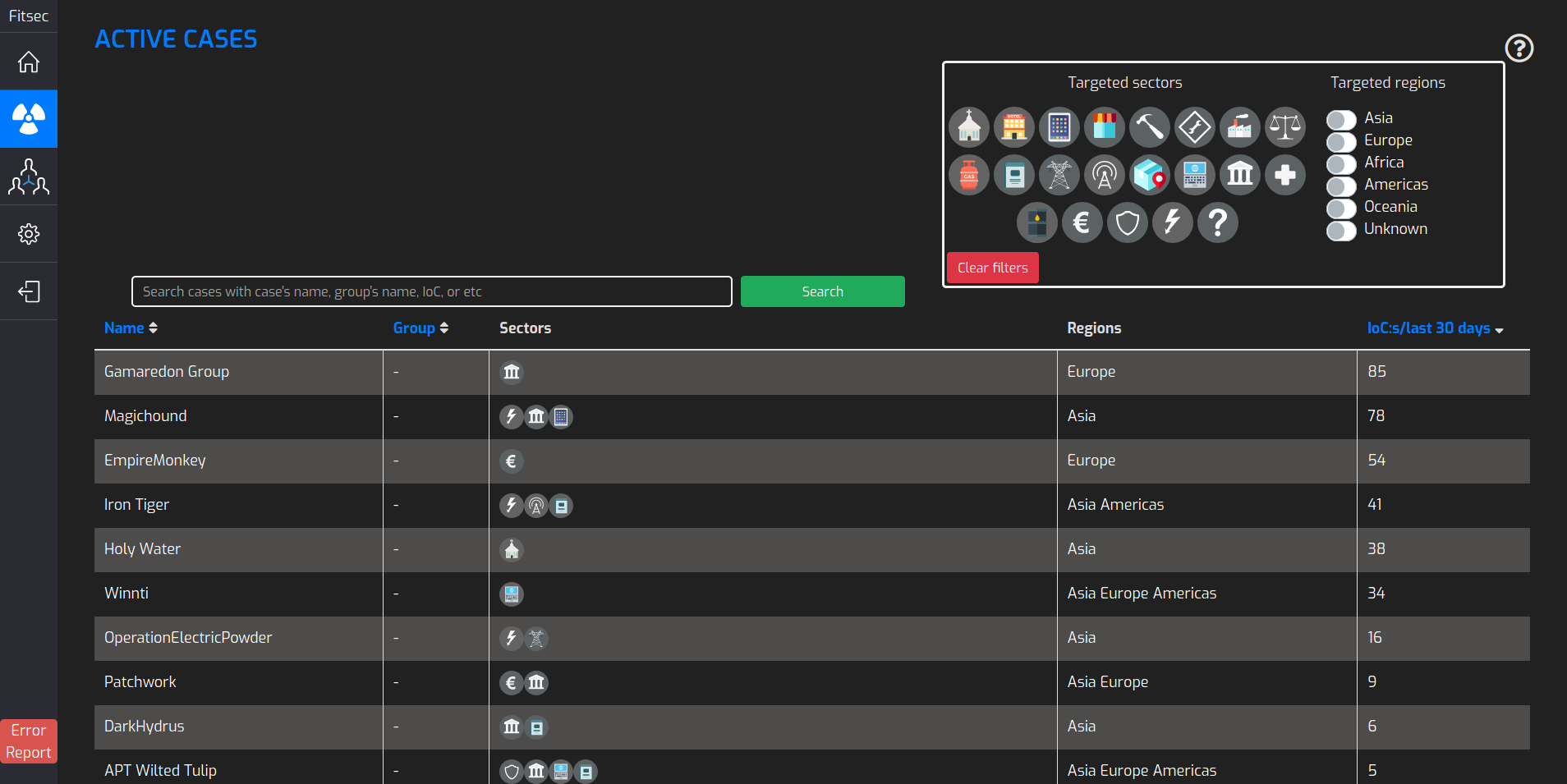
SandboxIOC-Feed
The Fitsec SandboxIOC feed contains network IOC data that gives detailed insight into malware C2 (command and control) servers, enabling your security team to do prioritized response against internal malware infections to prevent further damages from occurring.
The SandboxIOC feed is crucial to network operators, governmental institutions and other organizations who need to detect malicious behavior in the network perimeter before malicious activies damage their business.
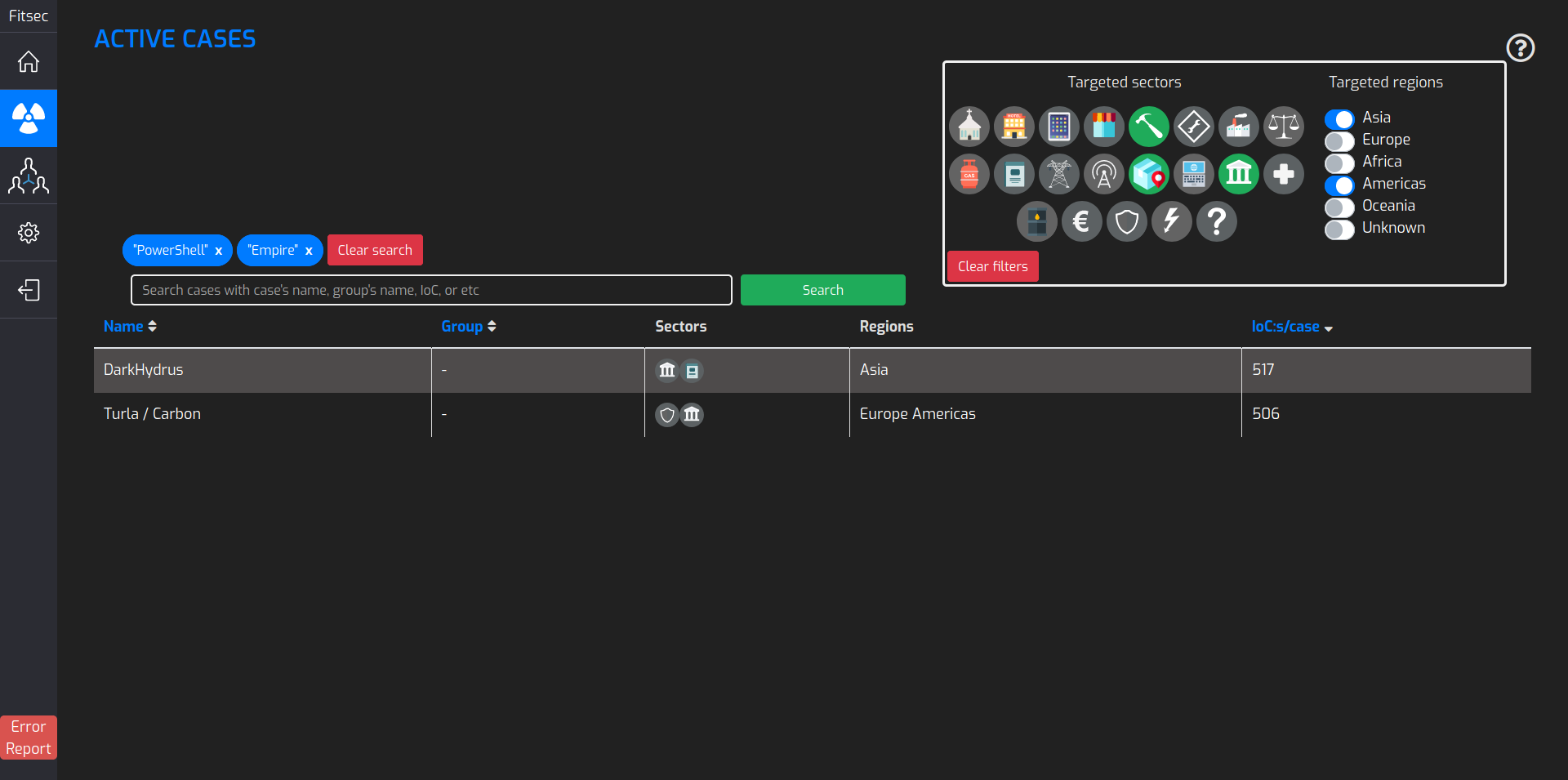
SinkholeIOC-Feed
The Fitsec SinkholeIOC feed listens to the traffic and detects the stolen data. As a client you will get BOT data such as infected IP addresses and information on the malware that has been detected. The Sinkhole feed provides actionable intelligence on
hundreds of thousands of infected, malicious systems globally.
The SinkholeIOC feed is especially beneficial to operators and Governmental Institutions, and for anyone else who has the need to locate malicious systems.